


Compliance, covered
Wix Studio is committed to the highest international privacy and security regulations. Our website security certificates include PCI DSS Level 1, SOC 2 Type 2, SOC 3 and several ISOs, and we’re compliant with GDPR, CCPA and LGPD.






THREAT PREVENTION
Secure from the core
Security is woven into the platform by design, so every site is automatically built on a safe foundation, with maximum protection from the get-go.
Secure software development
At every step of the development process, we use security best practices—like design and code reviews, threat modeling and penetration tests—to ensure a safe platform.
Safe data encryption
Our data in transit encryption uses HTTPS, TLS 1.2+ and automatic SSL, while data at rest uses AES-256—the strongest encryption standard commercially available.
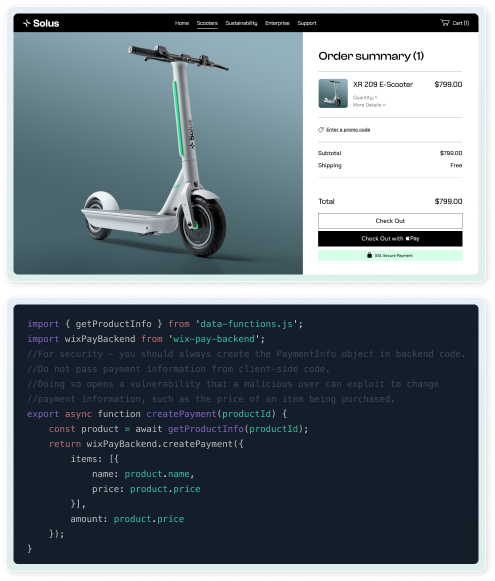
Secure payments & anti-fraud
All Wix Studio sites are compliant with the highest Payment Card Industry Data Security Standards (PCI DSS), supported by anti-fraud protection, to safeguard payment info and protect transactions.
Third-party risk management
Wix Studio operates a strict TPRM Program, including ongoing assessments, to ensure vendors align with our security standard.




SOC & SIEM
Our experts in the Security Operations Center work 24/7/365 with advanced system information and events monitoring to detect and respond to threats, faster.
Anti-DDoS
protection
Immediate detection and response to DDoS attacks mean your sites stay resilient and available.
Security
visibility
We invest in top-notch tools and technologies to achieve high visibility of our security posture, so we can keep operations secure across our entire platform.
Data
analysis & ML
This innovative, signature approach uses machine learning to detect pattern changes and suspicious activity, in order to block any attempted misuse of your accounts, data or sites.
Bug Bounty
program
We work closely with independent security researchers to detect and address any vulnerabilities in our platform.
RAPID RESPONSE
Protection when it’s needed most
The success of any website depends on its availability and continuity. That’s why our response plans are designed to keep sites up and running, in any situation.
Incident response
In case of emergency, our dedicated IR team is highly trained to establish a plan of action and rapidly respond to cybersecurity threats.
Business continuation plan
To ensure secure Wix Studio operations during potential disruptive events, our teams have a BCP that outlines steps for reliable continuation and smooth recovery.
Periodic training & simulations
We perform regular BCP simulations to prepare each of our teams for quick action, so you can continue to run your business—uninterrupted.
Account security
Get extra protection—and peace of mind—with our account security features.
Social login
Wix Studio supports Facebook and Google SSO for individual users.
MFA
We offer multi-factor authentication via email, SMS, phone call or authenticator app, plus 2FA via the Wix app—so users can add layers of protection to their account.
Login activity
Users can review their account login activity and change the password or log out of all devices if they see a device they don’t recognize.
Roles & permissions
Control user access by granting predefined roles or custom permissions to different users, and define which tasks and data they can access.
Site Member validation
Users with membership sites can choose to validate new members via email verification.
Email verification
All new users can confirm their email address after signing up, and can update it at any time from Account Settings.
ENTERPRISE SOLUTION
Enhanced security for big businesses
Allow employees and independent business units to log in with their organization credentials using top providers like Azure, Okta, Auth0, Google and more.
Secure your business systems and assets by adding, managing or deleting IP addresses and ranges for enhanced access control and security.
Keep a full audit trail of user activities across the entire organization, including any changes to sites and assets, to assist with debugging and regulatory compliance.
Use SCIM to securely automate the exchange of user identity data between your company's cloud applications and Wix.
.png)
.png)
ENTERPRISE SOLUTION
Data locality for enterprises
Enterprises can choose to store and process custom data elements in their own private clouds within a defined geographic boundary. And, store specific collected data on local servers by connecting to an external database using code. No matter where data is stored or processed, we ensure that it’s kept as secure as if it was our own.
.png)




